Advanced Security Configuration - Unicorn Perimeter Security (IDS configuration)¶
Creation of a Ruleset¶
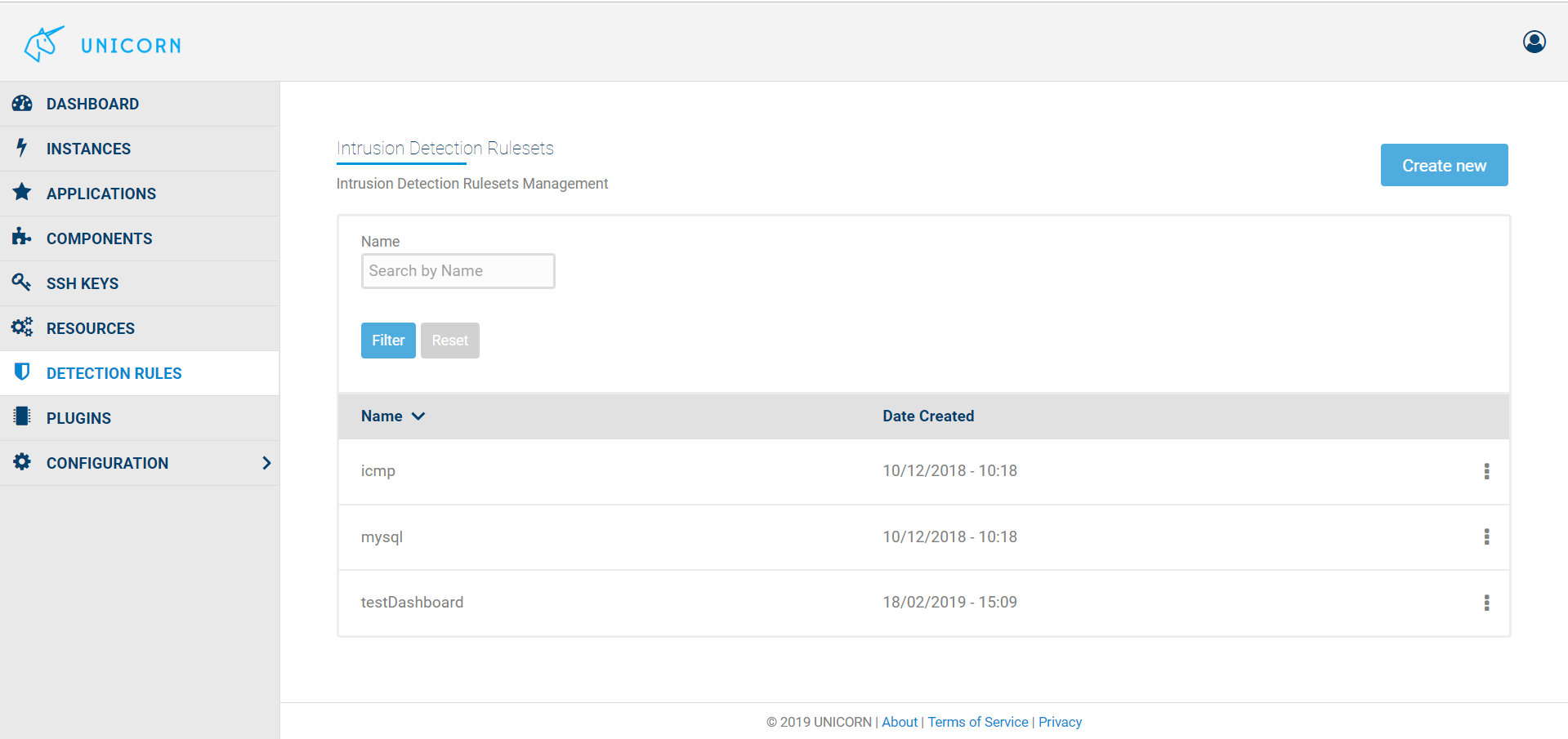
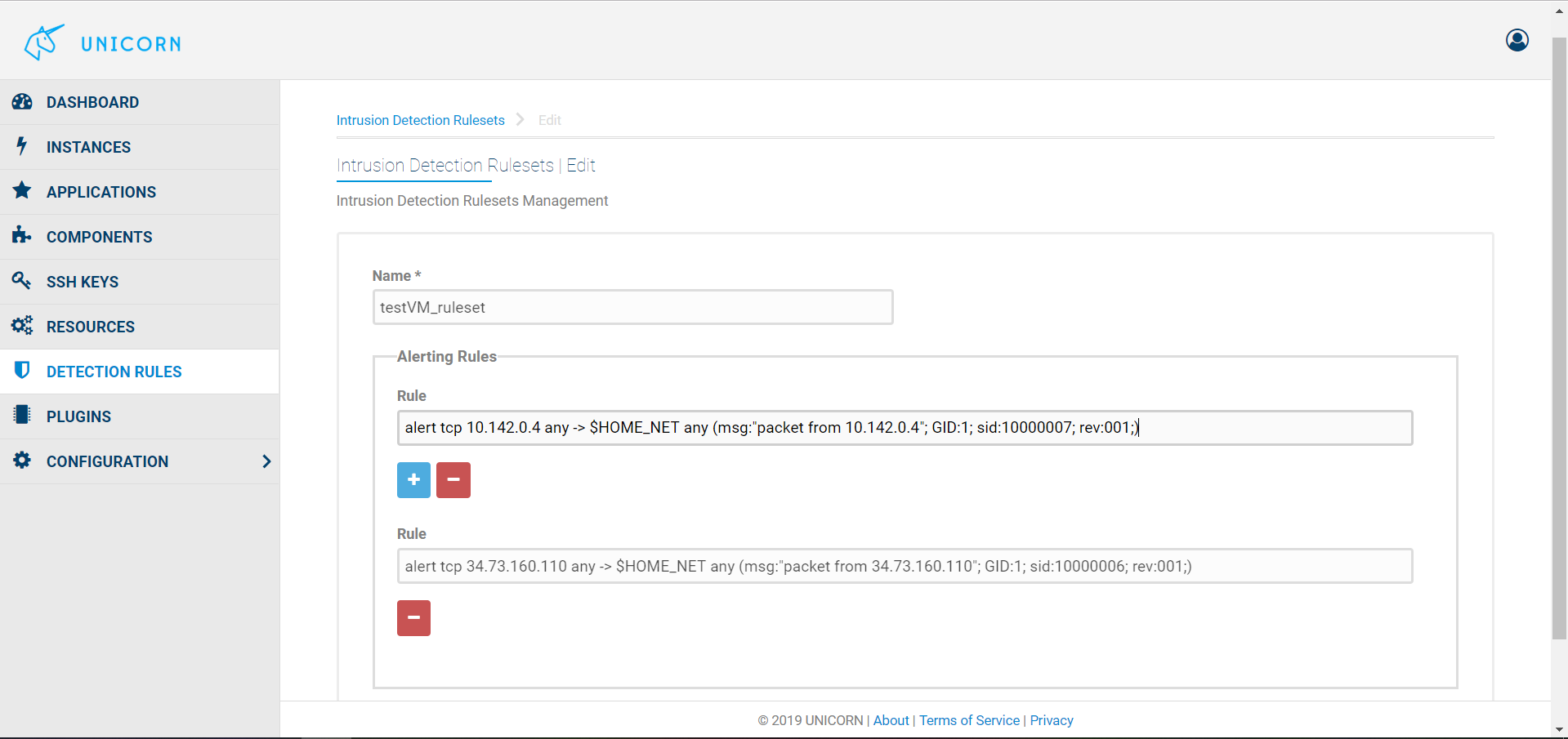
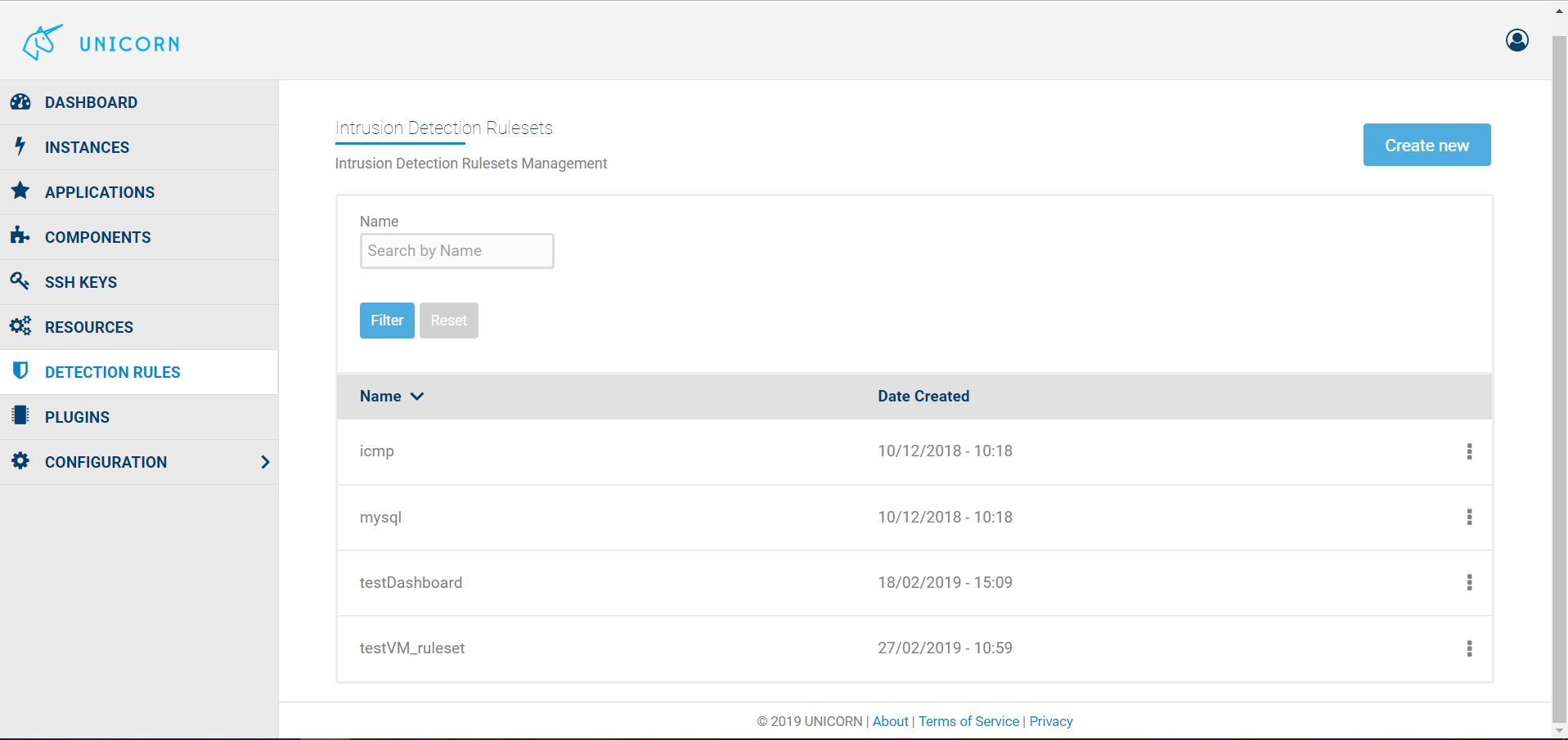
Unicorn Dashboard allows users to create their own Rulesets. The Detection Rules link opens a page with all the already available Rulesets (icmp, mysql, testDashboard), as is shown in the first Figure below. The Create new button leads the user to a new page where a new Ruleset can be created. What is needed is a name for the identification of the new set of rules and then the rules themselves. Each rule signature is written in the Rule Name box and the plus button adds the rule to the Ruleset. The second figure depicts the creation of a new such Ruleset named testVM_ruleset. A rule that raises an alert every time a packet comes from the public IP of the testVM is already included and a new rule raising an alert for every packet with the private IP of the testVM is about to be added. The third Figure shows again the already available Rulesets with the addition of the testVM_ruleset.
Configuration of an application component¶
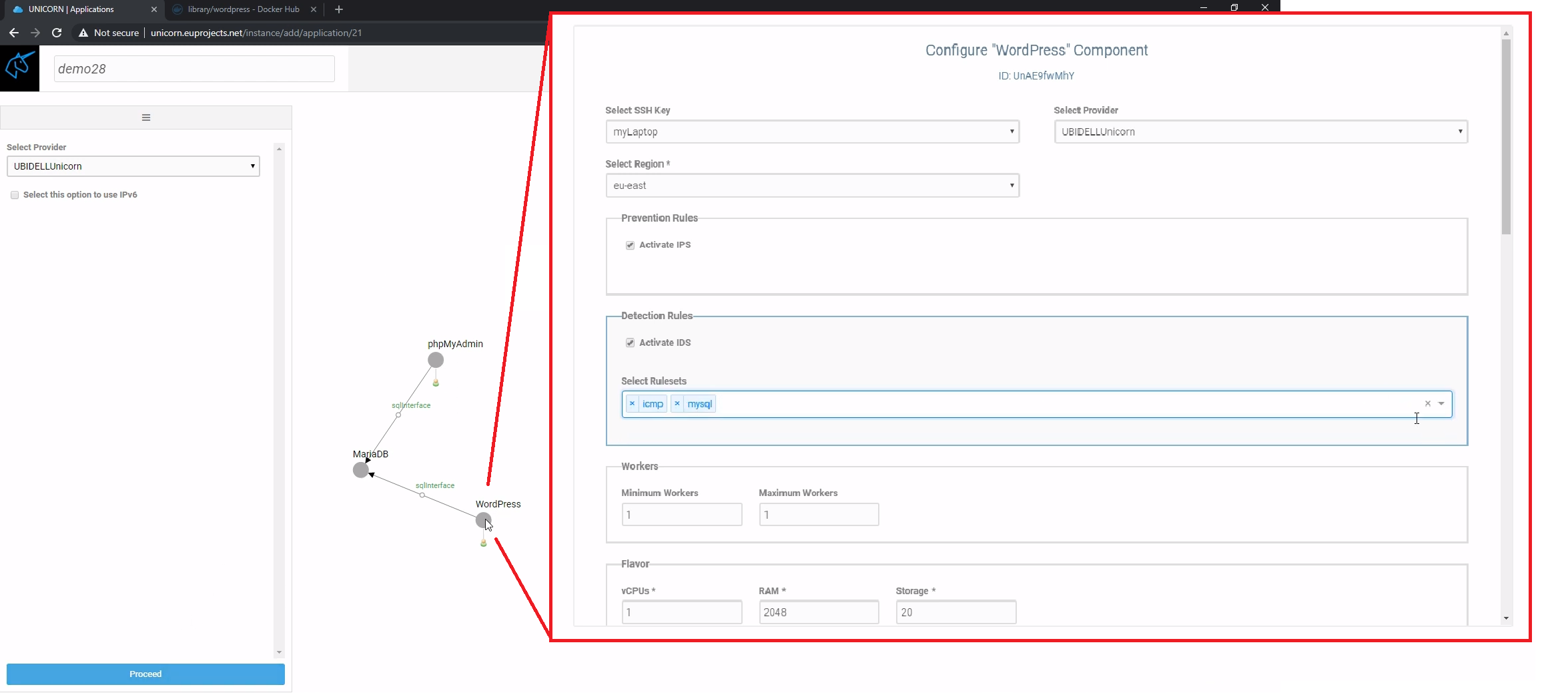
During the process of application initialization, a Unicorn user is able to configure any of the participating components of the application by clicking on the corresponding node of the service graph. The forth Figure depicts a service with three components (nodes). An overflow window appears when we click on the component that interests us, which allows for the activation and deactivation of the impended intrusion prevention and detection mechanisms (IPS, IDS) by selecting the appropriate check box. In the Figure both IPS and IDS are activated. IDS corresponds to a Snort instance that is containerized and deployed in the application execution environment. Such a Snort instance can be configured with different rule categories, which include a number of Snort rules, aka Rulesets. The process of creating a Snort Ruleset has already been described above. The user can choose, through the Unicorn dashboard, any of the Snort Rulesets from a dropdown menu. In this dropdown menu except from the Rulesets created by the users, there are predefined fine-grained Rulesets with rules that cover narrow vulnerability exploitation attempts, and broader Rulesets organized in two level. A detailed description of the offered Snort Rulesets is given in deliverable D4.2. As the forth Figure depicts, two Rulesets have been selected for Snort to use, icmp and mysql.
Set and unset Rulesets during application runtime¶
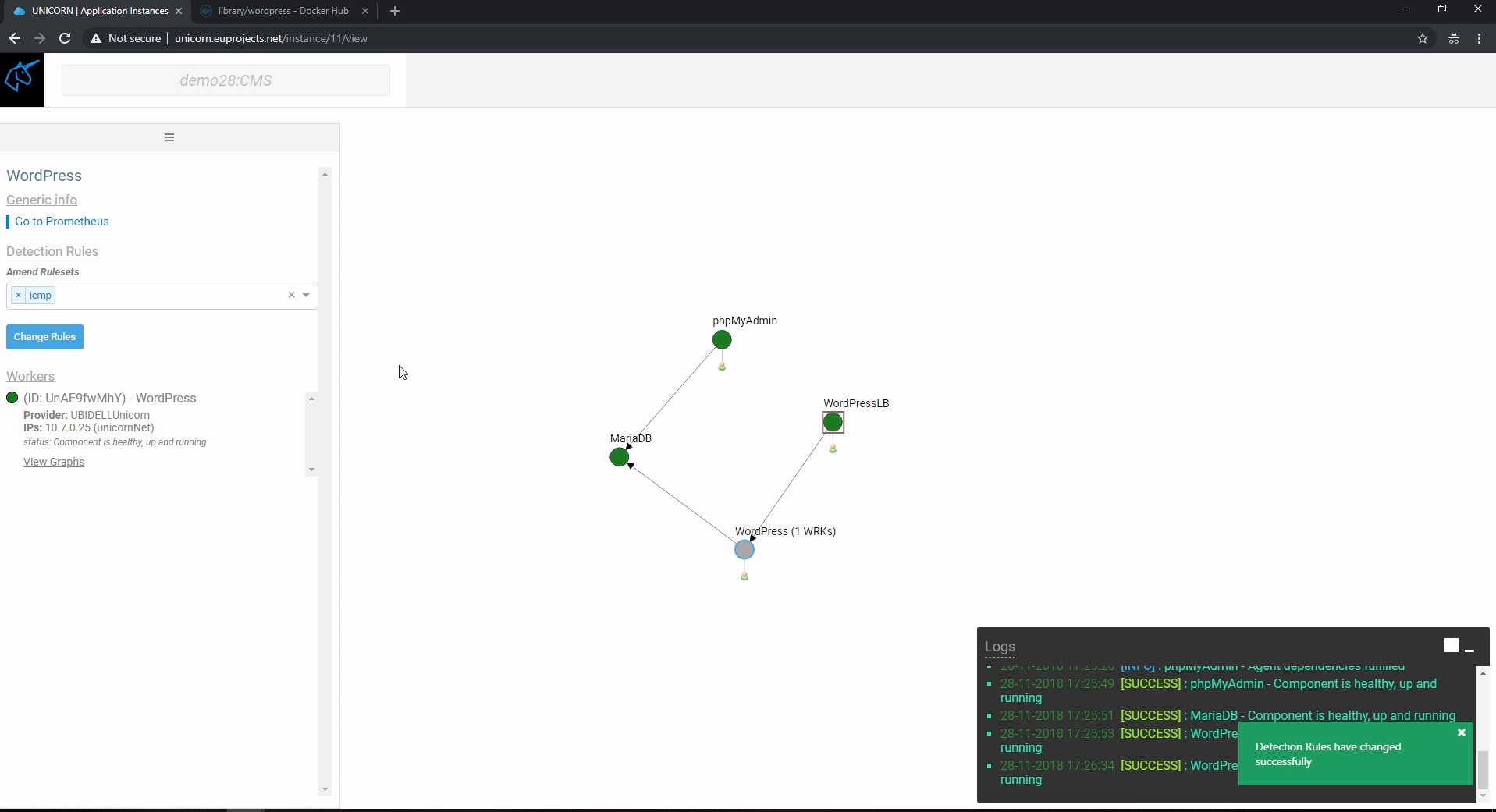
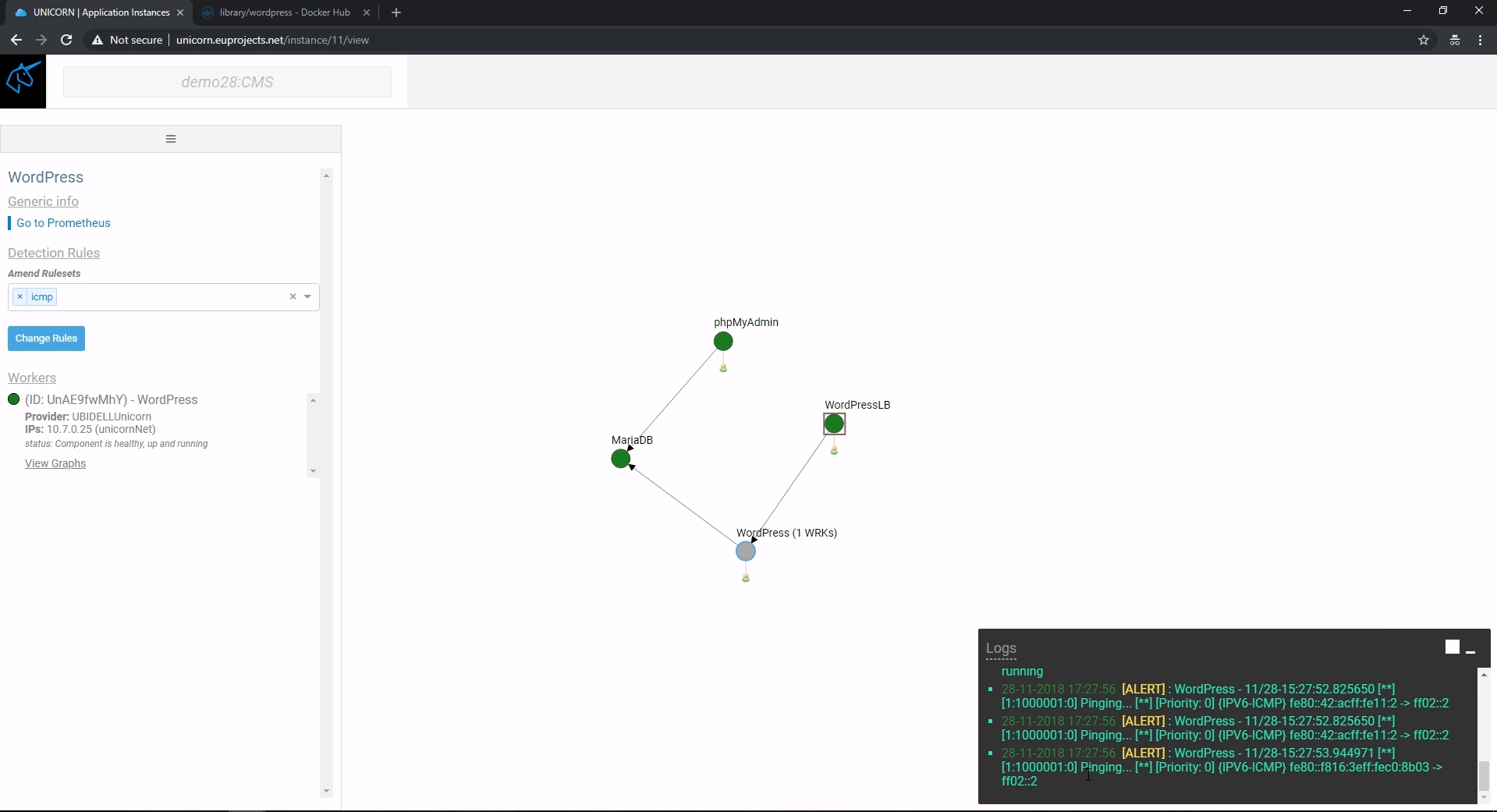
Provided that the IDS is already enabled during the application initialization, the user can set and unset Rulesets even when the application is running as can be seen in the fifth Figure. A Ruleset that raises alerts every time an ICMP packet reaches the node is selected in the fifth Figure. The green information box at the down right corner of the screen confirms the user’s selection. As a result, when PING requests reach the node alerts are created by Snort and are shown in the Logs window (sixth Figure). Multiple Rulesets can be active at the same time.